  |
|
|
Customer Support | Products | Company Info | Links | Helpdesk |
|
|
||||
| Home | |
| Products | |
| Reviews | |
| Demonstration | |
| Testimonials | |
| Photos | |
| Specifications | |
| FAQ | |
| Press releases | |
| Download | |
| Legal Disclaimer | |
| Affiliates | |
| Distributors | |
|
|
Interface Security Keyghost II Standard
Written
By: evilcthul
Date submitted: 19/02/01
Type of Article: Product Review
Independent Review: Acid Hardware

Product Rated: 9.5/10
Introduction
If you saw an EMC Balun hanging off your keyboard's wire you'd hardly be surprised. Who could blame you? What's so surprising about a mere EMC Balun? It wouldn't even warrant a second glance. What if i was to tell you that this particular EMC Balun was actually a Keyghost? You'd probably start to get a bit worried. If I told you that the Keyghost could log up to 2,000,000 keystrokes with 128bit encryption in its Pro flavor and up to 500,000 keystrokes with no encryption in its Standard flavor you would have good reason to be worried.
The Keyghost is basically just a pass through cable for your keyboard with an EMC Balun in the middle. There is no way to tell that this EMC Balun is happily logging your every move. Unfortunately we are not at liberty to show you what this amazing little device looks like. You would actually be quite shocked if you saw it. There are absolutely no discernible markings. The faux EMC Balun actually houses all the circuitry the Keyghost needs to function including one non volatile ROM chip. This ensures that when the power is turned off to your system. The data logged by the Keyghost will not be lost. Here is a rough representation of what the keyghost looks like:
![]()
This product is definitely more suited toward the business market as there is not much need for a Keylogger in a home environment unless you deem it absolutely necessary to backup what you have typed. I find it useful in this situation as I have personally had Microsoft Word crash unexpectedly only to learn that I lost 3000 odd words of my essay. There is an obvious application for this device in criminal/computer crime investigation and intrusion detection. This device could also be used to detect employee fraud at a company.
Great Its a Keylogger...
This isn't just your standard keylogger. It is completely operating system independent. It is a hardware solution rather than a software solution. From the moment you turn the computer on and your BIOS cycles through the RAM to the moment you turn it off. This keylogger will not stop logging unless its memory is full. There is also no way to foil this keylogger unless you physically unplug it. Even then, it will not divulge the secrets of its log. All the Keyghost needs to function is a text editor and a PS2/AT keyboard. It will not work with USB keyboards. You can even make the keylogger deliver its log with "edit.com" in DOS, using a bootdisk.
So Why Don't I Just Download a Keylogger?
A lot of software "spy" keyloggers will just store their contents in plain text in an obscure place on your hard drive. Having the log stored in plain text or anywhere on the same hard drive for that matter could pose quite a serious problem if someone was to find it.
The commercially made software keyloggers also have their major shortcomings:
1. They cannot be installed without administrative or very lax privileges
to a machine.
2. A software solution would not be able to log any BIOS attempts, whilst
the Keyghost can.
3. Being software based they are detectable by the operating systems for
example a Windows keylogger typically functions as a VXD or virtual device
driver. If the user was suspicious enough to check for hidden devices
he would soon find the keylogger.
4. Sometimes it is not practical to have non uniform logging methods within
a company as different computers could be running different operating
systems the Keyghost is an elegant solution to this problem.
5. A software based key logging solution could take a performance hit
out of the system it is running on as it must write to a file on the hard
drive and take up a slight amount of valuable memory space.
6. If a machine is running more than one operating system the log will
not be continuous.
7. As a user's awareness of the software around them grows they may suspect
they are being logged.
After considering this the software solution begins to look more and more unattractive. However, it does have a few benefits over the Keyghost in that it can store a huge amount of keystrokes far exceeding 2,000,000 depending on the target computer's hard drive size. The software solution in most cases is also free which may be more attractive to home users. In some cases the software keylogger can also email the log contents to a predefined email address. However, there is always a risk with software of losing the logs due to system failure.
Packaging
The review unit was sent via FedEx and arrived within 2 days. This is speedy to say the least. We are based in Australia and the product was shipped from New Zealand. This is a shorter distance than NZ to USA. You can expect the Keyghost to get to you pronto. It came in a package which was very similar to a software box. It had about the same dimensions. It is fully padded inside the box and should not break during transit. The box includes the Keyghost unit and some adaptors if you plan to use it on an older style AT keyboard.

Installation
If god gave you two hands to install a Keyghost you would quite honestly only need one to install the Keyghost. It's an absolutely trivial experience to install the Keyghost. Plug one end into the keyboard the other end into the PS2 connector on your motherboard. If you have an older style AT keyboard the process is the same except you'll need to attach the DIN adaptors to the ends of the Keyghost.
|
Before
Installation
|
After
Installation
|
 |
 |
|
For security reasons, the photo (above right) is only a representation of what the KeyGhost looks like. The actual KeyGhost II is injection moulded to look exactly like an EMC Balun. |
|
Keyghost In Action
One thing I must say is I'm impressed with the way the Keyghost has functioned. It works exactly as advertised and all problems that Dan claimed to have with his unit have disappeared. This leads me to believe that Interface Security is not resting on its laurels and continually updates the firmware as my version was probably newer than Dan's (v6.3.8). In addition to this if there is a major firmware update Interface Security will upgrade your unit for you free of charge. That is great customer dedication by anyone's standards.
Typing the default password of "vghostlog" in any text editor will present you with a menu like this:
This menu is typed by a phantom typist. It can be used anywhere from "notepad" to "vi." Any text editor will do.
vghostlog
[C] safe mode
*** KeyGhost II Standard v6.3.8
www.keyghost.com
Menu >
1)
Entire log download
2) Section log download
3) Wipe log
4) Format memory
5) Options
6) Optimize speed
7) Password change
8) Diagnostics
9) eXit
Select >
Hitting any other key apart from the numeric choices will put the Keyghost back into silent mode. Displaying this message:
Now logging ...
If the password combination is not entered at all the logger will happily sit in the background waiting for the password to be keyed in and save all the key strokes made. The password can be set from anywhere between 8-12 characters. This unit we are reviewing has no encryption algorithm so would be electronics enthusiasts could quite possibly open the unit and download the contents of the log off the Flash ROM chip. These problems are fixed in the slightly more expensive Pro version of the Keyghost.
With 128bit encryption it is highly unlikely that anyone would gain access to the unit if they did not know the password. It would take literally years and years of computing time for even the world's largest computers to crack the 128 bit encryption used. This option is definitely attractive for people wishing to keep the log secret.
A quick explanation of the functions of the Keyghost:
1) Entire log download - Initiates the Ghost Playback function where it will start to repeat all key strokes from start to finish from the logs. If a key is pressed in this time the Keyghost will abort.
2) Section log download - Same as above except you can choose where to begin the log dump from.
3) Wipe Log - Delete the current log.
4) Format Memory - If there is an error inside the Keyghost's memory this optional will delete all data stored and hopefully remedy the problem.
5) Options - Allows you to set whether or not the logger logs arrow keys.
6) Optimize Speed - Allows you to set how fast the ghost playback function types back the keystrokes. On most modern computers you can use the maximum of 150 Characters Per Second (CPS) but on some slower machines you may have to change the speed.
7) Password Change - Allows you to change the current password. This erases the logs though.
8) Diagnostics - Checks the memory inside the unit for faults.
Logs
This paragraph is dedicated to showing you what the Keyghost would log during a normal pattern of usage for various applications and situations where it would be used in.
Typing
***
KeyGhost II Standard v6.3.8
www.keyghost.com
Menu >
1) Entire log download
2)
Section log download
3)
Wipe log
4)
Format memory
5)
Options
6)
Optimize speed
7)
Password change
8)
Diagnostics
9)
eXit
Select > 1
- key to stop -
Keys so far is 224 out of 104672 ...
Dear AcidHardware.com reader,
This is a test message to show you the benefits of the keyghost. It really is a remarke<del><lft><del>able piece of technology.
vghostlog
Wipe log (y/n) ? n
Cancelled.
Please note in the above example I made a slight typing mistake and it registered the non standard character keys I pressed. It detected the delete key, left arrow and then the delete key again. I will not include the menu again in further examples. I will only include the logged text.
Sequence Of Arrow Keys Keys so far is 640 out of 104672 ...
<lft> <rgt> <rgt> <lft> <upa> <upa> <rgt> <dwn> <lft> <rgt> <rgt> <lft> <upa> <upa> <rgt> <dwn> <lft> <rgt> <rgt> <lft> <upa> <upa> <rgt> <dwn> <lft> <rgt> <rgt> <lft> <upa> <upa> <rgt> <dwn> <lft> <rgt> <rgt> <lft> <upa> <upa> <rgt> <dwn> <lft> <rgt> <rgt> <lft> <upa> <upa> <rgt> <dwn> <lft> <rgt> <rgt> <lft> <upa> <upa> <rgt> <dwn>
This would be a very typical log of someone playing a First Person Shooter
on your computer.
It could also navigating around an excel spreadsheet.
Random Log Of Non Alpha-Numeric Keys
<ctrl-alt-del> <alt-x> <alt-c> <ctrl-p> <'F1> <F12> <del> <ins> <hom> <pgu> <pgd> vghostlog
These two examples illustrate how the Keyghost notates non alpha-numeric keys.
Finally being a very intelligent unit the Keyghost compresses key strokes. For example say a user presses the down arrow as they're scrolling down a page 200 odd times you won't have to sort through 200 instances of .
Compressed Key Strokes
Keys so far is 128 out of 104672 ...
((117x))zzzz(z(68x)) ssss(s(90x)) pppp(p(103x))
This not only saves space on the Keyghost it also saves you having to sift through pages and pages of logs. If arrow keys do not suit your purpose you can turn them off via the keyghost options:
Options >
1) Arrow Keys Recording: On
Select or [enter] to exit > 1
Options >
1) Arrow Keys Recording: Off
Select or [enter] to exit >
This can make things like Excel spread sheets less cryptic to read. Changing any other options like deleting the log is very simple with the intuitive menu. The menu system is quick and efficient.
Keyghost Accessories and Software
So you've just bought the standard 500,000 stroke Keyghost. You haven't checked the log for a week and now its full. You have to sit there for 10-12 minutes waiting for the log to happily scroll by. This can be very frustrating as the PS2 port is only capable of delivering 150CPS maximum. This is where the Turbo Download adaptor comes in. It allows you to hook the Keyghost unit to your serial port and download the log at 57600bits instead. This means that you can dump logs in an instant to a text file. Note: The software however is only Windows compatible for this option. The Turbo Download Adaptor is a great idea if you only want to check the logs on weekly/monthly basis. The Pro SE, Pro and Std versions of the Keyghost are compatible with the download adaptor. If you wish to purchase one it is $49USD.
Secondly there is another highly useful but totally optional piece of software. It is a log analyser. It attempts to change the seemingly meaningless logs into something a bit more meaningful. It can also sort through logs to get vital pieces of information. You can find the software here. For Example:
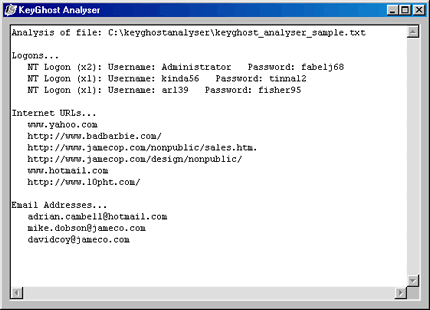
Was generated from:
Administratorfabelj68
www.yahoo.comhttp://www.badbarbie.com/ kinda56tinna12 adrian.cambell@hotmail.com
I'm uploading the design files to the public web server now, could you
get them for me? Its the one we used last time but I changed the password
to atlanta69.
mike.dobson@jameco.comHi,
I calculated the sales figures that are projected for the next year. I
have put them up on our web server, under http://www.jamecop.com/nonpublic/sales.htm.
Administratorfabelj68davidcoy@jameco.comHey, one more thing, I got hold
of some more files for the design team, I put them up on the web server
under http://www.jamecop.com/design/nonpublic/ arl39fisher95www.hotmail.com
http://www,l0pht.com/
Price Considerations
Since there really are no hardware solutions apart from the Keyghost we will look at a commercial software vs hardware solution comparison.
We are considering the following software's prices (all prices are correct at time of writing):
Invisible
KeyLogger Stealth for Windows NT4/2000 single computer license: Limited
Time Offer: $99 (Regular Price $149)
PC
Activity Monitor Pro $ 149.95 Stealth Keyboard Interceptor for Win NT/2000
$ 69.00
Hardware Options (correct at time of writing):
External KeyGhost II Std $99
External KeyGhost II Pro $149
External KeyGhost II Pro SE $199
Reputedly PC Activity Monitor Pro is the best software based key logging solution available. It also comes in at quite a premium at $50 more than the Keyghost II Standard. If you really don't need the ability to email the logs to an address automatically I would definitely prefer to purchase the Keyghost. For me, a hardware solution is always more elegant than software. It requires no overheads whatsoever. The hardware option always wins in my opinion. It's absolutely trivial to install and will work on any computer with a PS2/AT keyboard.
Comparing the two "Pro" units is where the price comes into serious consideration. We must take into account the time taken to research and develop the Keyghost into its current incarnation. While this price may seem considerably hefty to the normal user I would say that the price is very reasonable considering the level of support you receive from Interface Security. They have had regular firmware upgrades to alleviate problems with the Keyghost and will surely continue to update the firmware regularly until they have ironed out all problems that exist. Furthermore they are constantly developing software like the log analyzer which is completely free of charge. The "Pro" versions of the Keyghost are for the really keen users. I would suggest that you consider your decision to buy a Pro as the price is quite hefty. If you require the added features and security of the Pro unit it is a very good package.
Conclusions And Final Thoughts
If you have considered throughout this review that this unit is pure evil and I would love to log that ex/husband/enemy you have the Keyghost's purpose all wrong. If you totally disagree with what Interface Security is doing. I would probably imagine that various government agencies around the world have devised similar devices. Interface Security has just made the technology available to the masses. This leaves us with the point about privacy issues. I have deliberately left this point till the end. When you purchase this product from Interface Security you receive the following disclaimer:
"Using the KeyGhost to log/record other people's keystrokes or break into another persons computer without his/her knowledge can be considered as an illegal activity. It is the final user's responsibility to obey all applicable local, state, and federal laws. Our hardware is intended for authorized system administrators, employers, and/or owners of the computer. KeyGhost & partners, the device's creator, and it's employees assume no liability and are not responsible for any misuse or damage caused by our KeyGhost product. You must agree to the above, before purchasing a KeyGhost device."
Not only is it quite unethical to log someone else's key strokes it is also highly illegal. AcidHardware.com absolutely no responsibility for what you do with your Keyghost. Quite honestly though with a product this well disguised and an in-built into the keyboard model available there is really nothing stopping you from doing this. Apart from the fact you risk loosing up to $349USD worth of equipment if the person you are bugging finds out there is nothing stopping you at all. When was the last time you checked your keyboard to see if there was an extra EMC Balun? I must applaud Interface Securities for pricing the Keyghost unit responsibly. It discourages everyone running out and purchasing a unit just to spite someone. Their marketing of the unit reflects this also. If you are really going to consider logging someone you shouldn't be, this unit really isn't for you.
This product definitely services a very select market. Interface Security have a very well made quality product that fits demand perfectly. It works as promised and doesn't fall short in any aspects. If what you require is a hardware key logging solution you can't go past the Keyghost. In terms of compatibility, efficiency, practicality and ease of use the Keyghost excels in every department.
The Keyghost could be benefited though by allowing the unit to be contacted remotely and a smaller more discreet EMC Balun. These are not major problems and in its current incarnation the Keyghost is a worthy purchase. There is a covert version of the Keyghost which I believe is smaller and has a capacity for 120,000 key strokes. It does not have any playback functions and requires you to use the Turbo Download Adaptor.
I would like to take this opportunity to thank Jacob Katsipis and Despina Kerdemelidis of Interface Security. Without their assistance this review would not have been possible.
9.5/10
If a Keylogger is what you need this is "it".
Check out more reviews >>
