  |
|
|
Customer Support | Products | Company Info | Links | Helpdesk |
|
|
||||
| Home | |
| Products | |
| Reviews | |
| Demonstration | |
| Testimonials | |
| Photos | |
| Specifications | |
| FAQ | |
| Press releases | |
| Download | |
| Legal Disclaimer | |
| Affiliates | |
| Distributors | |
Interface Security KeyGhost II Keyloggers
Written
By: David (DataOrb)
Date submitted: 03 December 2000
Type of Article: Product Review
Independent Review: Geek Vortex
![]()
The name is bond, James bond.
What
I am about to tell you, should be kept confident, should not leave within
of this article. Think for a second about how many passwords you input
to your computer? Maybe One for your ISP? And Maybe One for your mobile
ISP? And let's not forget One for all of the discussion forums you frequently
visit. How much confident information you log into various web sites?
Perhaps your credit card number? Or maybe your phone number? How much
information you disclose about yourself? You think that information is
safe? Sure, with 128bit encryption algorithms, it might be hard to crack
your information out of the encrypted file.
And
might Years and Years of CPU time, But what I am about to tell you, might
shock you. There is really no need to. That's right, there is no need
for hundreds of cpu and man power to gain access to the confidential data
you store on your computer. What if I told you that there is a little
white box INSIDE your keyboard that logs anything you type? Are you scared?
Are you ridiculing this idea? "No such things exists", and if does, only
used by the CIA or FBI? Well, think again. I got into my hands, a VERY
dungarees item. Something, that perhaps shouldn't have even been created
in the first place. But it is here. And nothing is going to change it.
So you better get to know it. Knock Knock neo. You are being watched.
![]()
Ever head of the term "Key Loggers"? they are nasty pieces of software that will record and monitor about every letter you type in that keyboard of yours. And when the time is right, with a simple command, the EVIL individual who installed that software on your computer, can retrieve the entire log, can retrieve the entire content of a mouth (or perhaps even more) worth of typing, via the net, or physically being at your computer. While software key loggers were around for a LONG… LONG time, since the early days of DOS and UNIX, but they always had the limitations involved of actually being installed on a computer hard disk. Which means you must boot the computer, log as a user WITH install and modification permissions, install the software, and hope that no conflicts will arise from the installation, conflicts that might give the user you are trying to monitor hints that something is strange, that something is not quite all right.

The
KeyGhost Box
So here enters the "Sovereign" class starship of KeyLoggers. The KeyGhost. But this round, it's not software based. It's hardware based. The KeyGhost is a revolutionary product, a simple 30cm long cable with a white cylinder at the middle, that when is connected to a computer, LOGS EACH AND EVERY keystroke a user enters. And can spill it all on demand, Form the same terminal being monitored, or from a computer 50km away. All you need is a computer terminal with a PS/2 port and a text editor. No need for software.
|
Before
Installation
|
After
Installation
|
 |
 |
|
Installation of the KeyGhost, simply plug it into the PS/2 port. |
|
No need for external drivers, No need to to reboot computer. No need for any special action. Simply connecting the KeyGhost to a PS/2 Keyboard port will activate it. Allowing it to feed power from the host computer (no need for any external power connector, no need for a battery, no need for an outlet), and will quietly, in the background, without ever interfering with the computer operations, without taking any system recourses will start logging every keystroke the user enters.
And in the end of the day, when the user begin monitored logs off from his terminal, thinking no one will ever get access to sensitive information, you walk by the computer, pull the KeyGhost from the PS/2 port. And take it home. Once you arrive, all you need to do connect it to your computer PS/2 port, go into a text editor, and type the default password. "Vghostlog" In a single word. Without making a backspace, and to your instant sense of gratification, the KeyGhost operation menu will open up inside the text editor.
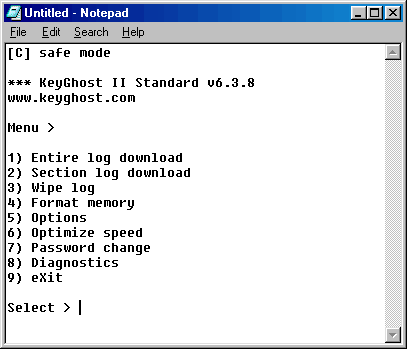
I think this menu is extremely straight forward. To access the entire log within the KeyGhost, all you have to do is hit number 1 in your keyboard, and to your amazement, EVERY SINGLE thing the user have typed in his computer, every single word, letter, will be displayed. The interaction with the KeyGhost menu is extremely easy and straight forward Like using old command prompt applications. The commands available:
C)
Safe mode - this will change the speed the text is retrieved from the
KeyGhost, to solve compatibility problems with old computers.
1)Downloads the entire recorded log from the KeyGhost Security Plug.
2)Downloads the log form a section you input. Let's say from char 872
and beyond.
3)Clears the information stored in the KeyGhost
4)Format memory - Clears AND formats the KeyGhost Memory.
5)Contains user selectable option such as - Arrow keys: select whatever
the arrow keys will or will not be displayed when a log is retrieved from
the KeyGhost.
6)Optimize speed - select the menu retrieval speed of the KeyGhost. Same
as safe mode [c], only this time you can select the delay between each
char in milliseconds.
7)Password change - will allow you to select a different password then
the standard "VGHOSTLOG"
8)Checks whatever the KeyGhost is working properly.
9)Exits the menu, returns the KeyGhost into it's logging mode.
The
KeyGhost is a very sophisticated piece of software, in the new version,
It now compress repeated keystrokes when they are stored, and displays
them in a "Short" form when they are typed back from the KeyGhost memory.
For example If a user types "Y" six times, the KeyGhost will later retrieve
it as "zzzz(z(2x))". This goes for arrow keys, as well. Someone scrolling
through a document with the down arrow won't eat pages of log, but just
come out as something like "((67x))". You can turn off arrow key logging,
if you like. With the 6th. Menu option. Quite smart if you ask me. While
the KeyGhost is a PS/2 "Adapter" there is an AT Port convertor, in case
you wish to use it on an old AT keyboard, and a USB version is in the
works. While the KeyGhost will be able to work perfectly WITH an adapter
attached to the Keyboard, such as an AT keyboard with a PS/2 Adapter (I
have tested this using my old Focus MM keyboard), it won't work if there
is any other kind of monitoring equipment attached to the keyboard you
wish to monitor, such as control overlays (plugs that can override keyboard
and mouse access of desktop terminals).
But beside this limitation, the KeyGhost works very good. Too good if
you ask me. It's so easy to operate and install it, that anyone can. Don't
you see that crucial implications involved in such a high breach in user
security? However, beside secret surveillance of other computers, the
KeyGhost can be also used for backup for your data. (Now you have the
perfect excuse to buy a KeyGhost!
"No… em… I use it to STORE data… yes! That's it!" :) If you are a writer,
and require a 3rd of a 4th Backup device, then the nonvolatile flash memory
inside the KeyGhost will prove as an excellent mean to back up your data.
It will record every single key you type, so if you are in a profession
that losing even a single keystroke typed means disaster, then viola!
You found another use for the KeyGhost!
The data inside the KeyGhost won't be erased, not even if the KeyGhost
is unplugged from the computer. And there is no "save" option, you don't
have to "save" the data into the KeyGhost/ no need to worry what information
is and what information isn't inside the KeyGhost. It's on the fly backup.
Without the hassle of CD's or cartridges. Or slow write / read times.
There
are various KeyGhost models, and the one I am here to review is the basic
one. The KeyGhost Home Edition. While "only" having the memory to store
128,000 keystrokes, it will add to about 20 hours of touch typing at 80
words per minute, which is more then enough for logging keystrokes throw
the day. Install the KeyGhost in the morning, and pick It up later at
night. But if say, you require longer periods of monitoring, there are
more professional models of the KeyGhost II available as well. With memory
of up to 2,000,000 Keystrokes, and 128bit Encryption (It's not really
128 bit encryption, because the character case password only gives you
398,541,260,467,162,000,000 possible combinations… "ONLY" :) these models
are perfect for long time surveillance of computer systems, without the
fear of the Data inside the KeyGhost getting tampered with. So it's very
safe to say, that while there is a **possibility** of tempering with the
keystrokes stored on the KeyGhost, no one that will snag that logger will
be able to find what keystrokes were logged without a use of a cluster
of 8-way processor Unix servers, AT LEAST.
The KeyGhost is a perfect solution for monitoring and harvesting sensitive
information, information that might not belong to you at all. Now, I don't
think I need to mention the EXTREMELY HIGH cases of moral problems involved
with such a thing. And using the KeyGhost, while gives you a HUGE EGO
boost, is something to take under advisement. You can't just wave your
hand and make the moral problems of using such a device go away. But if
such moral problems don't bother you (you Evil you! :), and you require
a simple, powerful, elegant solution to track down various information
on various computer terminals. You should go and get the KeyGhost II.
Any one of the models. Starting from the "Basic" PS/2 Adapters, and up
to Keyboards that are being sold with the KeyGhost installed inside. Impressive.
But remember, you are paying a heavy price tag for each key stroke this
thing logged, both in dollar terms (this thing is expensive!) and both
in moral price.
I really have really nothing bad to say about the KeyGhost as a product. It has a very easy installation, a very easy operation, and is extremely innovative as an idea.
To sum the KeyGhost in one sentence, "A Masterpiece of Engineering". Nothing more nothing less.
Pros:
- a perfect keylogger.
- independent of the computer operating system
- easy installation
- easy retrieval
Cons:
- pricey
Final
Mark: 10/10
![]()
Check out more reviews >>
