|
New
Product!
 KEYGHOST ADDS VALUABLE TIMEDATE STAMP INFORMATION TO THE LOG OF
RECORDED KEYSTROKES.
KEYGHOST ADDS VALUABLE TIMEDATE STAMP INFORMATION TO THE LOG OF
RECORDED KEYSTROKES.
Are
you losing productivity because you can't keep track of PC usage?
 Do you really
know how long your employees spend on-task?
Do you really
know how long your employees spend on-task?
 Can your business
afford to fund non-productive hours?
Can your business
afford to fund non-productive hours?
 Are you effectively
harnessing the huge potential of your work force?
Are you effectively
harnessing the huge potential of your work force?
If you don't
keep track of PC usage, alot of your business could be walking out
the door. And you may not even realise it!
 Keylogger discreetly records and TimeDate stamps everything typed,
including emails, chatroom activity, instant messages, website addresses,
internet searches and more...
Keylogger discreetly records and TimeDate stamps everything typed,
including emails, chatroom activity, instant messages, website addresses,
internet searches and more...
 Keep track of PC usage and monitor your sensitive PCs and data entry
terminals for backup and to detect unauthorized activity.
Keep track of PC usage and monitor your sensitive PCs and data entry
terminals for backup and to detect unauthorized activity.
  Pinpoint computer misuse, lost productivity and fraud.
Pinpoint computer misuse, lost productivity and fraud.
 Cannot be detected or disabled with software scanners.
Cannot be detected or disabled with software scanners.
 Can be unplugged and information retrieved on another PC.
Can be unplugged and information retrieved on another PC.
TimeDate
KeyGhost is the fastest way to monitor your company PCs!
No
software installation is necessary to record or retrieve keystrokes.
Patent
Pending built-in access menu for high-speed transfers.
 KEYLOGGER INSTALLS IN UNDER 5 SECONDS!
KEYLOGGER INSTALLS IN UNDER 5 SECONDS!
KeyGhost Time
and Date keylogger
plugs in between your keyboard and Desktop PC.
Tamper evident seals - included
- help detect unauthorized removal of KeyGhost.
TimeDate KeyGhost
SX is injection moulded inside solid black plastic so it looks exactly
like an ordinary adapter plug.
 PROTECT YOUR ORGANISATION
PROTECT YOUR ORGANISATION
If you don't
keep track of PC usage, alot of your business could be walking out
the door. And you may not even realise it!
Here is your
opportunity to see every keystroke that is typed on your company
PCs, and find out what is going on inside your company. Then you
can use this information, to keep your business running smoothly
and on-track!
Once installed, KeyGhost keylogger discreetly captures and records
all keystrokes typed, including chat conversations, email, word
processor, or even activity within an accounting or specialist system.
KeyGhost is completely undetectable by software scanners and provides
you with one of the most powerful stealth surveillance applications
offered anywhere.
Unlike software keyloggers that can be switched off or have their
stored keystroke data modified, stolen or erased, KeyGhost is an
unobtrusive hardware device and only you can read the data inside.
Because KeyGhost uses STRONG 128-Bit encryption to store the recorded
data in it’s own internal memory (not on the hard drive), it is
impossible for a network intruder to gain access to any sensitive
data stored within the device.
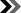 PATENTS
PENDING
PATENTS
PENDING
TimeDate
KeyGhost SX uses a Patent Pending
method to enable the highest speed transfer currently achievable
- over 450 characters per second
- without the need for special adapters, or even to unplug the device.
This is 3 times faster than the 'KeyGhost' and 'KeyGhost II' models.*
TimeDate
KeyGhost SX features Patent Pending
dual-mode time and date stamping allowing maximum flexibility when
configuring the recording of time and date information along with
the stored keystrokes. This improves memory efficiency and reduces
the time it takes to read and understand the recorded keystroke
log.
 RELIABLE + PORTABLE + SECURE
RELIABLE + PORTABLE + SECURE
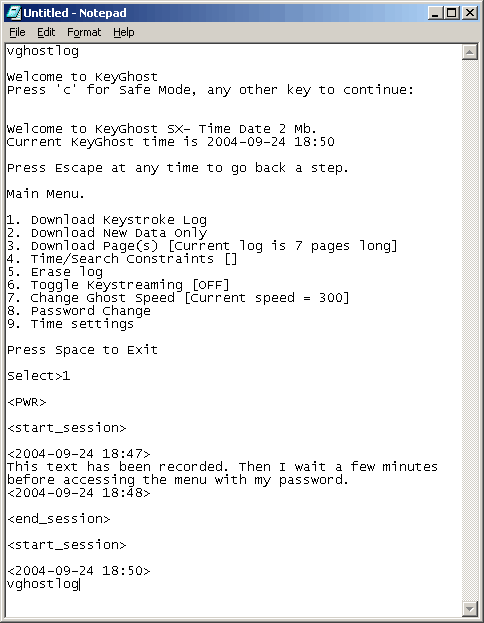
TimeDate KeyGhost’s
built-in ‘Ghost menu’ system
allows you to search, retrieve and privately view what has been
recorded using any standard text editor (e.g NotePad, WordPad...etc).
Retrieve
the recorded keystrokes by simply typing your chosen password
into any text editor. KeyGhost will recognise your password and
the 'Ghost menu' will appear as below:
Flexible
settings to configure allow you to tweak the TimeDate KeyGhost
SX device to your required specifications.
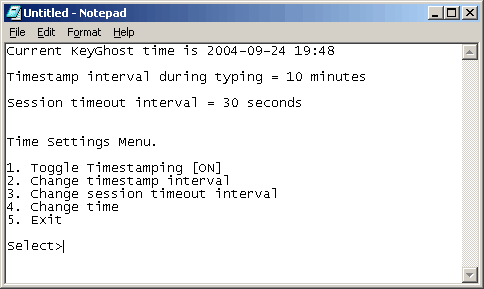
Below is an example of the Timestamping sub-menu, where you can
configure the 2 modes of time and date stamping. ('Interval' - a
regular pulse, and 'Session timeout' - grouping periods of keystrokes
activity): Patents
Pending
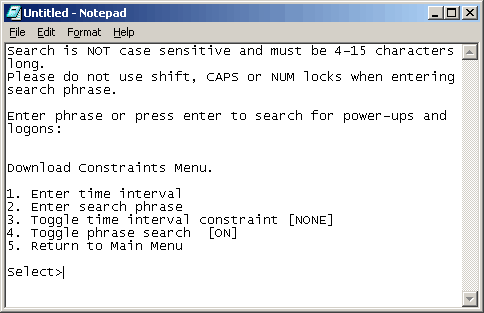
Search quickly
through the log with the Download Constraints menu. You can
use this menu to quickly search through the log by instance of keyword
(search phrase), or between periods of time (to the closest hour):
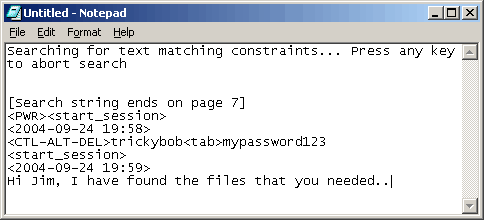
Finding powerup
and logon activity is a breeze. Just select option 2 of the
Download constraints menu, press enter, and return to the main menu
to quickly isolate and download the relevant user information:
 KEY BENEFITS
KEY BENEFITS
 Easy to install in a few seconds! Simply plug it in and record everything
that is typed on the PC. One of the most powerful keyloggers available.
Easy to install in a few seconds! Simply plug it in and record everything
that is typed on the PC. One of the most powerful keyloggers available.
 No new software to install or learn.
No new software to install or learn.
 Keystrokes can be retrieved on the spot – or unit can be unplugged
for retrieval on another computer. (Portable hardware keylogger)
Keystrokes can be retrieved on the spot – or unit can be unplugged
for retrieval on another computer. (Portable hardware keylogger)
 Impossible to detect or disable using spyware and software scanners
(SpyCop, Who’s Watching Me...etc).
Impossible to detect or disable using spyware and software scanners
(SpyCop, Who’s Watching Me...etc).
 Stores many months worth of keystrokes in non-volatile flash memory
(same as in smart cards) that doesn't need batteries to retain storage.
Stores many months worth of keystrokes in non-volatile flash memory
(same as in smart cards) that doesn't need batteries to retain storage.
 Works on all desktop PCs & all PC-compatible operating systems (Windows,
Linux, Dos...etc).
Works on all desktop PCs & all PC-compatible operating systems (Windows,
Linux, Dos...etc).
 Uses no system resources. Keylogger will not slow down or affect
the PC.
Uses no system resources. Keylogger will not slow down or affect
the PC.
  WHO IS USING KEYGHOST?
WHO IS USING KEYGHOST?
 As a security tool for computer fraud investigations.
As a security tool for computer fraud investigations.
 As a monitoring device for detecting unauthorised access.
As a monitoring device for detecting unauthorised access.
 As a deterrent, to prevent unacceptable use of company resources.
As a deterrent, to prevent unacceptable use of company resources.
 As a back up tool which creates a log of all keystrokes typed on
a keyboard.
As a back up tool which creates a log of all keystrokes typed on
a keyboard.
Read more 
 KEYGHOST SX: REVIEWS
KEYGHOST SX: REVIEWS
|
RoboPimp
Hardware Review: KeyGhost SX 512KB
by Tom on April 1, 2004
World Class Security and Audit Tool...
The
first thing you'll notice is that it's tiny. After it's plugged
in, you can hardly tell it's there. Spy enthusiasts will love
its discrete profile, and all users will appreciate its unobtrusiveness.
All
in all, the KeyGhost SX is easily one of the best security
tools in any users arsenal.
The
ease of use, compatibility, security, and practicality of
the KeyGhost SX make for an amazing and essential product
for anyone...
Review Score: 9.5/10
|
Read
more KeyGhost SX Keylogger
Reviews 
Kit Includes:
KeyGhost SX Keylogger. Instruction sheet. Warranty card. Tamper
evident seal.
Example notification banner as recommended by U.S. Department of
Justice.
 PS/2 KEYBOARDS ONLY
PS/2 KEYBOARDS ONLY
System Requirements: Desktop IBM PC compatible. PS/2 (small
round plug) keyboard.
KeyGhost
SX works on ALL PC operating systems (Windows 95,98,ME,NT,XP,2000
Linux, Beos, OS/2, Dos, Sun Solaris).
* Patent Pending
high-speed transfer mode - 'KeyStream'™ - will work with most
modern Desktop PCs.
> PLEASE
NOTE: For USB keyboards (small rectangular plug) please choose KeyGhost
USB Keylogger.
|

